
Testing IoT Innovation Virtual Seminar
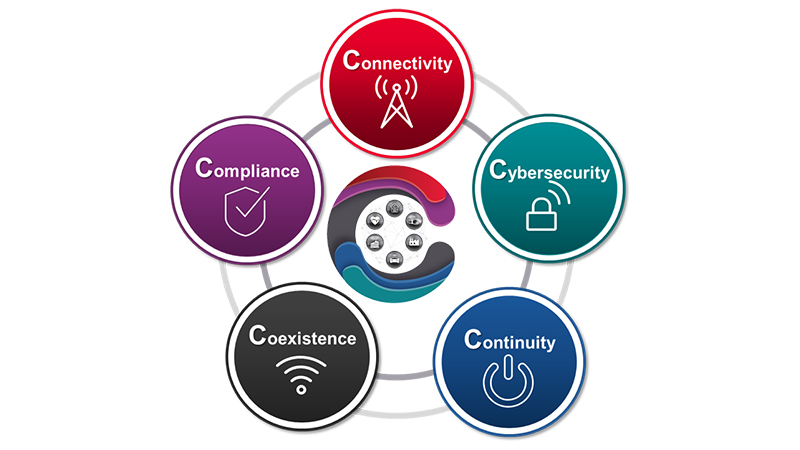
Gain insights into the multi-faceted challenges of designing and testing your IoT devices by applying the 5 C’s of IoT: Continuity, Connectivity, Compliance, Coexistence and Cybersecurity. Join Keysight technical experts in this 2-part virtual seminar to help you conquer the 5 C’s of IoT.
Live & On Demand Webinars
Testing IoT Innovations: Insights into Connectivity & Continuity (Part 1)
Duration: 2 hours
Available On Demand
Part 1: Insights into Continuity and Connectivity
Continuity requires extended battery life for your IoT device. Learn how to measure highly dynamic current and identify critical RF and DC events that consume the most power. Get fast insights into battery life and learn a better way to power your devices during test and development.
Connectivity testing ensures a strong, robust, foundation for IoT devices to connect to other devices and network at large. Learn about the various IoT wireless technologies (like LoRa, NB-IoT, LTE-M, Wi-Fi, ZigBee® and Bluetooth®), test challenges, and solutions that simplify testing from R&D to manufacturing

Testing IoT Innovations: Insights into Compliance, Coexistence & Cybersecurity (Part 2)
Duration: 1 hour, 50 minutes
Available On Demand
Part 2: Insights into Compliance, Coexistence and Cybersecurity
Compliance testing verifies that your IoT device meets evolving wireless regulatory standards which enable access to markets in various geographies. Learn about the two main categories of compliance tests, how to reduce your risk of failure and keep within budget and schedule.
Coexistence testing ensures that an IoT device can successfully operate in a crowded spectrum with other wireless devices. Learn how to assess the potential risk and the ability of the device to successfully maintain its functional wireless performance (FWP) in the presence of other interference signals.
Cybersecurity starts with products that are designed, built, and validated, to be secure. You can validate product security with an automated, repeatable methodology, that fits within your development processes. Discover the latest tools to assess and test your product against attacks, allowing you to find and fix vulnerabilities before shipping your products.
Learn more about our commitment to privacy: Keysight Privacy Statement
© Keysight Technologies
© Keysight Technologies